With the advance of the digital era and most of information being stored in online platforms, importance of cybersecurity increases day by day. In recent years, we have witnessed a number of data breaches that affected millions of people.
Yahoo breach that affected 3 billion people in 2013, the U.S. voter registration records of 191 million people that were leaked in 2015 and the Equifax breach that affected 143 million people in 2017 are just a few examples which show companies and governments alike can be the target of data breaches.
After 2015, the election of 2020 was more secure than ever, and it seemed like U.S. government had a good understanding of cybersecurity and had the means to detect attacks and breaches.
However, the recent SolarWinds breach has proved that the government and companies alike still lack the necessary precautions and failsafes to protect themselves from cyberattacks.
What Is SolarWinds and SolarWinds Breach?
SolarWinds Inc. is an American software development company with offices in several different countries. Their main focus is on monitoring computer networks for overloads, crashed servers and network connections.
An important point that separates SolarWinds from other firms is this: A number of federal agencies and almost all Fortune 500 companies are their clients, meaning that a great deal of important information is monitored through their software.
So, if a group with malicious intent wished to somehow sneak into the government and private systems to steal data, doing this through SolarWinds software rather than trying to individually breach the securities of tens of different agencies and firms would be much easier. This is precisely what happened with the SolarWinds breach.
SolarWinds breach is the most recently discovered breach of information which happened through one of the company’s products called Orion, used by around 33,000 customers in both public and private sectors. Company defines Orion as ‘a powerful, scalable infrastructure monitoring and management platform designed to simplify IT administration’.
Who Is Behind the Attack?
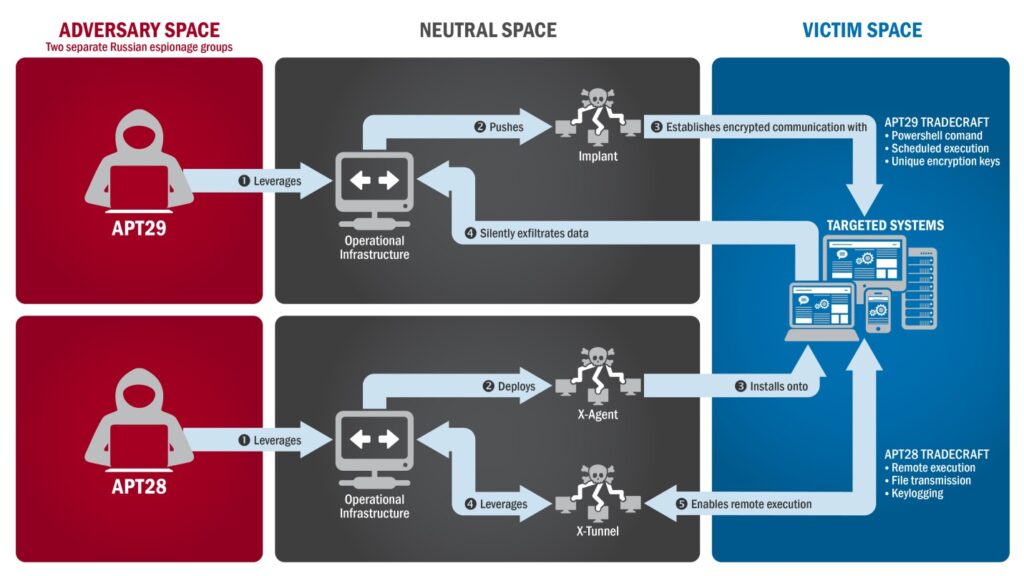
Russian hacker group Cozy Bear, who are believed to be part of Russian foreign intelligence service are thought to be behind the attack. Russian authorities, on the other hand, are calling these reports baseless.
U.S. Federal Government classifies them as advanced persistent threat ATP 29. Their profile is consistent with silent data exfiltration. You can see a basic schematic of how they work above.
You may think that such a breach would be accompanied with apparent signs and trails that would lead back to the hackers that we see in movies all the time: Computers crashing, alarms going off and whatnot. However, that was not the case at all. What happened was, users downloaded an update for SolarWinds’ Orion software, an update which had been corrupted by hackers to include a backdoor into the systems they were downloaded on.
Looking at the scope of the hack, about 18,000 users in private sector and the government are estimated to have been affected by this corrupted update so far.
This breach goes to show the importance of cybersecurity and risk assessment measures that should be employed by governments and companies.
How It Went Undetected?
Companies are mainly focused on stopping digital attacks and are under the misconception that they will never be breached, says Hitesh Shesh, CEO of a cybersecurity threat detection company. Due to this misconception, threat detection and response have lower priorities. As a matter of fact, it was reported that officials were not aware of the breach for at least 9 months until a private cybersecurity firm informed them of the issue.
The private firm, FireEye, realized they had been hacked and found out the attack was on a much larger scale while they were scanning their systems to find the source of the breach.
This just goes to show how damaging it can be to not have countermeasures in place for when your systems are actually compromised.

What Was the Goal?
Although the extent of the attack is still being investigated, State, Treasury and Commerce Departments, as well as the Department of Homeland Security and Pentagon are reported to have been compromised.
From what has been gathered so far, primarily the email accounts of Commerce and Treasury departments have been monitored through the hacking. However, considering the hack happened some 9 months ago and has only been discovered recently, the real amount of the information taken will most likely take much longer to determine.
From FireEye, hackers stole ‘sensitive tools that the company uses to find vulnerabilities in clients’ computer networks.’ The firm also reported that none of this stolen data appears to have been used for attacks on the U.S. government. On the other hand, whether these tools will be used for attacks in the future remains to be seen.
What Could Have Been Done?
This breach is different from previous cyberattacks due to the shear amount of time it took for people to realize it had happened at all. At the age we are living in, you have to think that ‘anything that connects to the internet is hackable’, says Jay Bretzmann, who is the security products program director in International Data Corporation, and this incident proves him absolutely right.
This breach has affected firms and agencies with possibly the best protections in the world, which goes to show that approaching cybersecurity issues from a single aspect is not enough. Trying to make your systems unbreachable is just impossible. You must have proper tools in place to understand when you have been hacked and have a roadmap for responding to the breach.
You have to wonder if things would be different if these establishments employed means of real time risk assessment to check their systems. What if they utilized 3rd parties to find ways to breach their systems to see where their vulnerabilities are? If they are doing these things, what if they did them more often so that they had real-time scanning of their security systems?
Although what ifs are useless at this point, it is clear that more precautions should be taken as soon as possible to ensure such events do not take place again in the future.